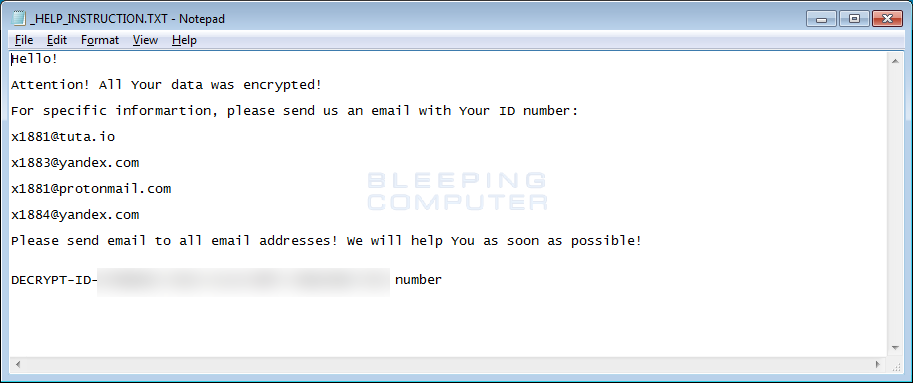
While the encryption methods stay the same in this variant, there have been some slight differences. The ransom note is still named _HELP_INSTRUCTION.TXT, but now uses the x1881@tuta.io, x1883@yandex.com, x1881@protonmail.com, x1884@yandex.com emails for a victim to contact for payment information.
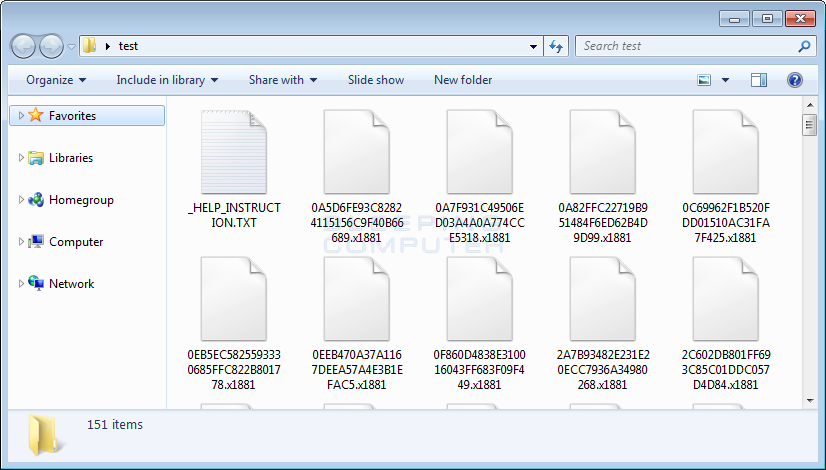
The next noticeable change is the extension appended to encrypted files. With this version, when a file is encrypted by the ransomware, it will modify the filename and then append the .x1881 extension to encrypted file’s name. For example, a test file encrypted by this variant has an encrypted file name of 0D0A516824060636C21EC8BC280FEA12.x1881.
This variant also contains 11 public RSA-1024 encryption keys that will be used to to encrypt the AES key used to encrypt a victim’s files. This allows the ransomware to work completely offline with no network communication. This variant’s 11 public RSA keys are the same as the previous Shark Cryptomix Ransomware variant.
In order to protect yourself from the x1881 variant of CryptoMix , or from any ransomware, it is important that you use good computing habits and security software. First and foremost, you should always have a reliable and tested backup of your data that can be restored in the case of an emergency, such as a ransomware attack.
You should also have security software that contains behavioral detections such as Emsisoft Anti-Malware or Malwarebytes. Regardless of the security software you use, make sure it contains behavioral detections so you do not have to rely on signatures or heuristics.